With the advent of Bitcoin and cryptocurrencies we acquire the ability to be our own banks, with the set back that we don’t acquire natively the ability to safeguard it.
As banks evolved in their security measures throughout the years we also need to keep up the pace on security measures. It is upon ourselves to safe keep our digital assets, therefore if we intend to be our own banks, we need to keep thieves at bay by keeping up to date with latest advancements on digital-assets-thievery, so we can take measures to avoid being a victim.
Threats
Malware
Malware or malicious software, is a blanket term for any kind of computer software with malicious intent. Most online threats are some form of malware.
Malware is all about making money off you illicitly. Although malware cannot damage the physical hardware of systems or network equipment (with one known exception, it can steal, encrypt, or delete your data, alter or hijack core computer functions, and spy on your computer activity without your knowledge or permission.¹
How to avoid malware?
Most importantly install antivirus program on your devices, this will help detect and remove potential malware threat that might want to steal your private keys or hijack your devices to mine cryptocurrencies.
Secondly, avoid clicking and opening shady looking websites and emails. At all cost avoid clicking on random pop-ups, and do not download anything from unfamiliar providers.
Phishing
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
The information is then used to access important accounts and can result in identity theft and financial loss.²
How to avoid phishing?
It is close to impossible to avoid interaction with phishing emails, simply because spam filters are not flawless. Many times we have to deep dive in the trash can that is the spam filter folder, to look for legitimate emails that should have arrived without problem to the inbox.
When opening emails that come from sources that are not white-listed, rollover the mouse over the links within the email to see where they will take you.
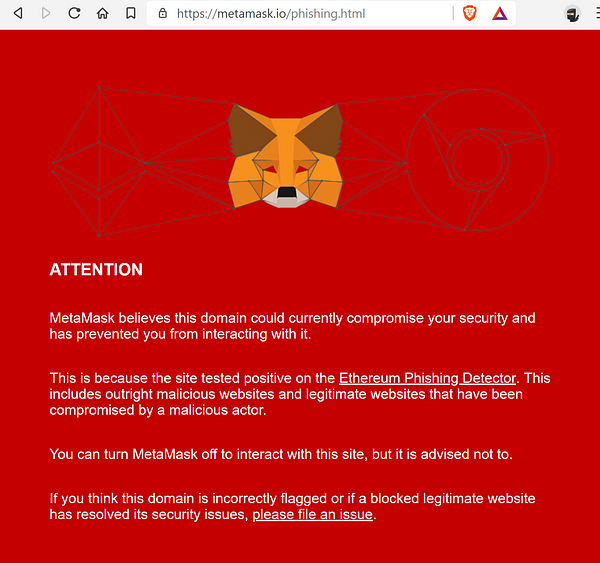
Legitimate websites should have SSL certificate, look that the link have HTTPS at the beginning of the URL, also look for misspelling within the hyperlink.
I like to recommend people to use MetaMask, it does a really good job at spotting phishing site, even though it’s not its main purpose.
Judgement should be your first line of defense, phishing attempts usually appeal to fear in case you don’t take immediate action, and greed for a “once in a lifetime opportunity”, if its too good to be truth, it might not be that good. Be skeptical of everything you receive on your inbox.
SMS 2FA
2FA (second factor authentication) is the use of two independent mechanisms to verify the identity of a user, in this case an SMS (text message) with the access code will be sent to your mobile.
In most countries is very easy to port a phone, meaning somebody that is not yourself could claim your phone number, and divert every call or SMS (text message) to a new device, change your password and get access to your accounts.
How to avoid SMS 2FA?
Opt-out of using SMS 2FA and instead go with a software authenticator such as Google Authenticator or Authy. Even safer are the hardware token, and push notifications through app, unfortunately not all websites offer it.
Juice jacking
Juice jacking is a term used to describe a cyber attack wherein malware might be installed on to, or data surreptitiously copied from, a smart phone, tablet or other computer device using a charging port that doubles as a data connection, typically over USB.⁴
How to avoid juice jacking?

Avoid at all cost plugin in your laptop or mobile USB devices or cables of shady precedence, might be hosting a malware, or spyware with keystroke logger, which can compromise your digital assets.
Best way to avoid juice jacking on your mobile is by carrying a personal battery backup for charging up…
Or wear a USB condom on your power cable.
Data snooping over VPN
A VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more.⁵
Trustworthiness of VPN’s companies has been put to doubt, due to latest reports on data snooping over VPN by service providers.
How to avoid Data snooping over VPN?
If you have the technical knowledge you could build your own VPN. But if you are not technically capable of creating your own VPN, you could use the Tor browser, which enables anonymous communication, but expect sub-par speeds, and UX.
There are some thrust-less VPN solutions like Sentinel (beta phase) and Orchid (under development), that could be the defacto VPN solution in the future, also Tor R&D hopefully will catch up to current market needs.
Passwords manager vulnerabilities
A password manager assists in generating and retrieving complex passwords, potentially storing such passwords in an encrypted database or calculating them on demand.⁶
Also password managers are vulnerable to hacking due to flaws on its code, as recently reported throughout mass media.
How to avoid passwords manager vulnerabilities?
If you are an avid password manager user, you might find that Trezor has an amazing hardware password manager, passwords are individually locked with the Trezor Password Manager, using your digital keys. Secrets are released one by one, and only after your physical confirmation on your Trezor.
Hardware Wallets Vulnerabilities
A hardware wallet is a special type of bitcoin (or cryptocurrencies) wallet which stores the user’s private keys in a secure hardware device.⁷
Latest reported vulnerabilities of hardware wallets in order to succeed to hijack your digital assets, need to have physical access of your device to install a bogus firmware to acquire PIN, and hack into the victim computer and wait until the PIN is introduced. This type of attack is unlikely to pose much of a practical threat.
How to avoid hardware wallets vulnerabilities?
Hardware wallet have very few vulnerabilities that we should be worried about, but here are a few recommendations:
- Buy directly from hardware wallet manufacturers, you want to avoid re-sellers who might be tempted to tamper with devices, there has been reported cases where hardware wallets are delivered with the passphrase already generated.
- Always make sure the address you are sending cryptocurrencies is the same as prompted on you hardware wallet, if its different you might be being subject to a MIM (Man in the Middle attack).
- Never leave your hardware wallet unattended or exposed to a third party access where it could be updated with an unwanted firmware.
- Keep your passphrase recovery in a different place than your hardware wallet, not on a digital form, but on paper, or even better on Titanium, and store on somewhere only you have access, i.e. a safe.
[1] https://www.malwarebytes.com/malware/#what-is-malware
[2] http://www.phishing.org/what-is-phishing
[3] https://www.techopedia.com/definition/10286/keystroke-logger
[4] https://en.wikipedia.org/wiki/Juice_jacking
[5] https://www.howtogeek.com/133680/htg-explains-what-is-a-vpn/
[6] https://en.wikipedia.org/wiki/Password_manager
[7] https://en.bitcoin.it/wiki/Hardware_wallet
Many thanks to TheCrypt0Mask, MisterCh0c, and AndrePreoteasa for helping me come up with the list and peer reviewing this piece!
If you enjoy the read, follow me on Twitter, is good for Karma.







Comments